Risk Management Systems
Risk management as a managed service ensures compliance and governance obligations are met.
Risk management as a managed service ensures compliance and governance obligations are met.
Information security strategy, risk mitigating security controls, and vendor assessments.
Identify security risks within your organisation, along side a mitigation strategy and treatment plan.
Privacy Impact Assessments, and strategies to minimise Breach Notification exposure.
Determine your organisations maturity against ISO 27001, HIPAA, EU GDPR Compliance.
Secure software engineering, bespoke security solutions and automating security in software development.
Collect, prioritise, track, assign and audit risks and corrective mitigations across the enterprise.
Risk management allow a structured, risk based approach to security expenditure. Ensure your security budget is addressing issues that ensure you meet your business goals.
Risk Management services range from ad-hoc and project based assessments, to enterprise risk management programmes to address board level and compliance obligations.
Catalyst Logic can work with your organistion provide security guidance that aligns with your business goals.
Should your business reqruire it is guidance to address identified risks, assistance with assessing the value and suitability security vendors products, or strategy to implementing controls to improve your security posture, we can work with your business to provide guidance around all aspects of information security.
Guidance can be provided as part of a project, or as part of a long term security strategy. Services include requirements gathering, business analysis, project management to ensure a sucessful implementation of your security programme.
Gain insight to the security posture of your organisation or department, with actionable advice on how to improve your security resiliancy.
A Security Health Check is often an effective intial step to improve your securiutiy posture. Utilsing assessment frameworks, customised to ensure relevance to your business, a Health Check can not only benefit from having another set of eyes to verify your security controls, but can uncover blind spots typically overlooked by internal staff.
All Health Checks produce a mitigation strategy, and treatment plan which can be actioned internally, or provide criteria for defining the success of external engagements.
Privacy data flows, impact assessments, and the development of a breach response strategy, are essential to understand your privacty risks, and minimise the likelihood and impact of a breach notification.
The Australian Privacy Principals (APPs), and the Notifiable Data Breach (NDB) scheme backed by the Privacy Act in Australia, and the General Data Protection Regulations (GDPR) in the EU have raised the bar for both the obligations and accountability in relation to Privacy for Australian companies.
Contact us to ensure you understand your eligability, obligations and steps towards ensuring you business has a strategy to ensure that you do not need to notify in the event of a data breach.
Determine your readiness for ISO 27001, Australian Privacy Principals, HIPAA, GDPR and Notifiable Data Breaches.
Gain insight into your organistiond maturity and ability to meet and exceed global Information Security and Privacy Standards.
Enterprise security architecture and engineering solutions spanning the fields of encryption, logging, event correllation, and API security.
Bespoke security architecture and engineering services can ensure that the gaols of your complex security projects are met from inception, through to certification.
Utilising Open Source solutions, and Application Programming Intefaces of propietary security products, and a rangew of programming languages as per your project requirements, Catalyst Logic can ensure delivery of your most demanding security projects.
Track compliance and infosec tasks through customised risk management, incident management, and remediation workflows.
Track operational tasks, managment projects and governance at the board level via dashboards that update as you meet your GRC goals.
Using Jira and Confluence on the Atlassian ecosystem, leverage a world class platform.
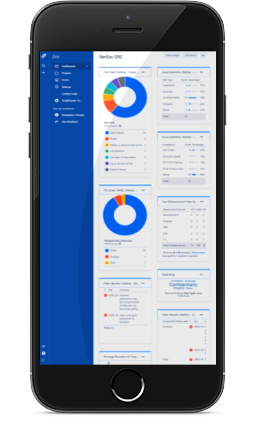
A high level of customistion across workflows, data collection, risk management, access control and security.
Integrate with your existing Atlassian platform, or access a fully managed secure, standalone platform leveraging its own customised faetire set.
See a return through reducued audit preperation, and external GRC engagements. All your complaince audit trails exist on a single platform.
Catalyst Logic provides security strategy and project guidance, independant vendor assessment, and ongoing support to ensure our clients meet thier information security goals.
James Keppel is a Certified Information Systems Security Professional (CISSP), and Certified Information Systems Auditor (CISA), with 10 years’ experience in the Information Security Industry.
Previously an Information Security Manager for an information management, and data protection company, spanning thirteen sites, James has overseen successful implementation of ISO 27001, ISO 9001, and PCI-DSS compliance. A specialist in developing and deploying software that assists engineering and technical teams manage their ISMS, incident, risk and network security needs, James’ broad knowledge of information security covers not only auditing and compliance, but technical implementation and remediation.
James’ professional industry memberships include ISACA, AISA, (ISC)², PPN and CSA.
© All Rights Reserved Catalyst Logic Pty Ltd